Phishing Scams: Identifying and Avoiding Online Threats
- Phone: +1(833)PHX-Geek
- 712 H St NE Suite 1904 Washington, D.C. 20002
Take a look at our camera system. Get remote access to your cameras, and monitor your restaurant while you are away. Great protection for you from theft, employee grift and wrongful lawsuits.
Introduction
Phishing scams are deceptive tactics used by cybercriminals to trick individuals into providing sensitive information, such as usernames, passwords, and credit card details. These fraudulent schemes often masquerade as trustworthy entities, hoping to lure unsuspecting victims into their traps. Understanding the fundamentals of phishing is crucial for anyone navigating the online landscape, as the threat continues to evolve alongside technology. 
At its core, phishing typically involves the use of emails, texts, or fake websites that appear legitimate. For instance, an email may appear to come from a reputable bank, instructing the recipient to click on a link and verify their account. However, these links often direct users to counterfeit websites designed to capture information. The rising sophistication of phishing techniques can make detection challenging, emphasizing the need for awareness and education.
Awareness is the first line of defense against phishing scams. By recognizing common tactics employed by attackers, individuals can adopt a proactive approach to safeguard their personal information. The goal is to empower users with knowledge, enabling them to identify red flags and make informed decisions when interacting online.
Phishing attacks come in various forms, each with distinct characteristics designed to exploit different vulnerabilities. The most common type is email phishing, where scammers send fraudulent messages appearing to originate from legitimate sources. These emails often include urgent requests or alarming news to provoke a quick response without thorough examination.
Another prevalent form is spear phishing, a targeted attack aimed at specific individuals or organizations. Unlike general phishing attempts, spear phishing usually involves extensive research on the victim, allowing scammers to create personalized messages that appear more legitimate. This approach can be particularly dangerous, as it increases the likelihood of success by building trust.
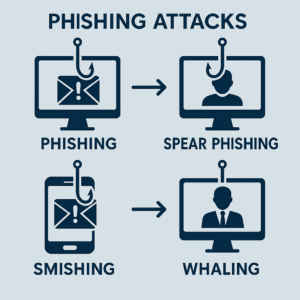 Whaling is an even more sophisticated variant of phishing that targets high-profile individuals, such as executives or leaders within an organization. These attacks often involve extensive planning and may use more elaborate social engineering tactics. Understanding these types of phishing attacks is essential for developing effective countermeasures and protecting sensitive information.
Whaling is an even more sophisticated variant of phishing that targets high-profile individuals, such as executives or leaders within an organization. These attacks often involve extensive planning and may use more elaborate social engineering tactics. Understanding these types of phishing attacks is essential for developing effective countermeasures and protecting sensitive information.
Identifying phishing attempts requires a combination of vigilance and critical thinking. One effective strategy is to scrutinize email addresses and URLs carefully. Scammers often use slight variations or misspellings in domain names to deceive users. By hovering over links without clicking, individuals can reveal their true destinations and spot potential red flags.
Another key identifier is the tone and content of the communication. Legitimate organizations typically maintain a professional tone and avoid using urgent language that pressures recipients into immediate action. If an email contains grammatical errors or awkward phrasing, it may be a sign of a phishing attempt. Always cross-reference the sender's email with official contact information to verify authenticity.
Moreover, implementing two-factor authentication (2FA) can significantly enhance security. Even if a scammer manages to obtain login credentials, 2FA adds an additional layer of protection, requiring a unique code sent to a user's device. By adopting these strategies, individuals can become more adept at recognizing and thwarting phishing attempts.
To effectively avoid phishing scams, adopting best practices is paramount. One of the simplest yet most effective strategies is to maintain a healthy skepticism towards unsolicited communications, whether via email, text, or social media. If an offer seems too good to be true or a request appears suspicious, it’s wise to verify its legitimacy through direct contact with the organization or individual.
Additionally, education plays a crucial role in prevention. Individuals should stay informed about the latest phishing tactics and trends, as scammers continually adapt their strategies. Organizations can enhance security by providing regular training sessions on recognizing phishing attempts and implementing security protocols tailored to their operations. 
Finally, utilizing security software and regularly updating it can help protect against phishing attacks. Many antivirus programs now include features designed to detect phishing attempts, providing an additional safety net. By being proactive and adopting these best practices, individuals and organizations can significantly reduce the risk of falling victim to phishing scams.
Conclusion
In a world increasingly reliant on digital communication, understanding and recognizing phishing scams is essential for protecting personal and organizational information. By being informed about the various types of phishing attacks, employing effective identification strategies, and adhering to best practices, everyone can contribute to a safer online environment.